Honor 7A (DUA-L22) слил
BACKUP SECURITY &
RPMB
Выложил в ресурс:
https://gsmforum.ru/resources/dua-l22-backup-security-rpmb.12354/
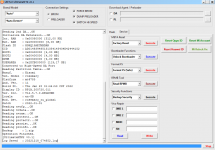
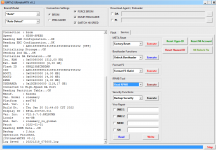
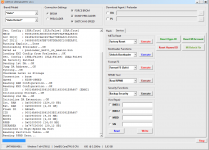
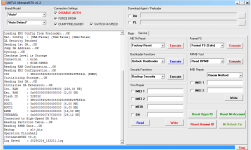
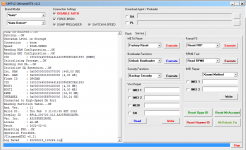
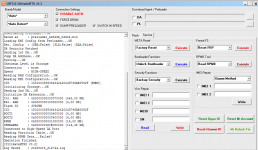
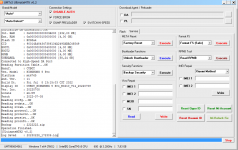
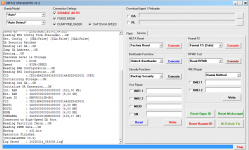
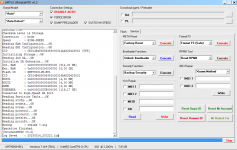
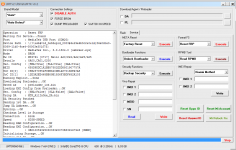
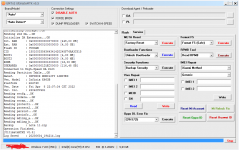
Operation : Read RPMB
Waiting for Device [BROM]...Found
Port : MediaTek USB Port (COM10)
Device Path : \\?\usb#vid_0e8d&pid_0003#6&3a6a7fd9&0&5#{86e0d1e0-8089-11d0-9ce4-08003e301f73}
Driver : MediaTek Inc., 3.0.1504.0 [usb2ser.sys]
Hw ID : MT6739 [0699] Unknwon
Details : 8A00,CB00,0002
Sec. Config : [SBA:True] [SLA:True] [DAA:False]
MEID : E825461030799FBEFA5754CB3511FD2C
SoC ID[0] : FE6D8F12FBDE7B9EF2BABCB74C252510
SoC ID[1] : 2EA6EA60444ACF86B011E527CDB3AADB
Running Exploit...Done
Downloading Preloader...OK
Saved as : preloader_dura64.bin
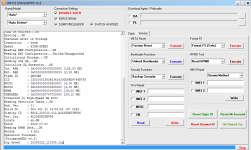
Loading EMI Config from Preloader...OK
Sec. Config : [SBA:False] [SLA:False] [DAA:False]
DA Security Patched
Sending 1st DA...OK
Jump DA Address...OK
Syncing...OK
Checksum Level is Storage
Connection : brom
Speed : HIGH-SPEED
Reading RAM Configuration...OK
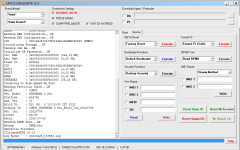
Reading EMI Configuration...
CID : 00000000000000000000000000000000 [UFS]
Initializing Storage...OK
Sending 2nd DA...OK
Initialize DA Extension...OK
Int. RAM : 0x00020000 [128,00 KB]
Ext. RAM : 0x80000000 [2,00 GB]
Flash ID : QE63MB
CID : 150100514536334D4204342FF22AC54D
BOOT1 : 0x00400000 [4,00 MB]
BOOT2 : 0x00400000 [4,00 MB]
RPMB : 0x00400000 [4,00 MB]
USERAREA : 0x3A3E00000 [14,56 GB]
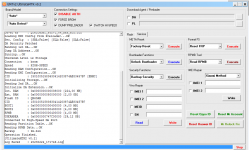
Connected to High-Speed DA Port
Reading Partition Table...OK
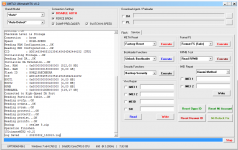
Brand : HONOR
Manuf. : HUAWEI
Model : DUA-L22
Platform : mt6739
Device : HWDUA-M
And. Ver. : 8.1.0
Prod. Name : DUA-L22
Build Dt. : Tue Dec 11 10:11:44 CST 2018
Display ID : DUA-L22 1.0.0.134(C10)
Ver. Inc. : 1.0.0.134(C10)
Locale : en-US
Patch : 2018-12-05
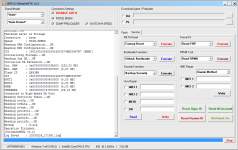
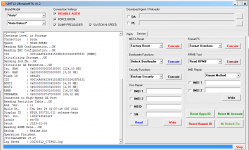
Reading RPMB Data...OK
Backup : 2.bin
Operation Finished.
[UltimateMTK2 v0.1]